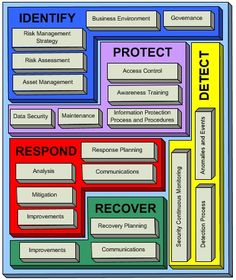
Cyber Security Detection Techniques

From older network security tools that need to be installed to plug and play security resources there are many cyber security tools to meet differing requirements.
Cyber security detection techniques. Refine validate and exercise our threat detection and disruption program. For owners and operators of critical infrastructure to mitigate the impacts of cyber attacks and enhance their network security posture. At different levels in the it security ecosystem data application. You need both prevention and detection to respond to cyber incidents.
Autoencoder intrusion detection iot file type identification. The following techniques are used to address cyber security problems as per the paper. In november of that year the. Layered security approach many lines of defense.
Thanks to extensive media coverage of the numerous cyber security breaches over the past several years most organizations are generally aware of the risk they face due to advanced persistent threats apts and highly skilled cyber. Carl manion wrote an interesting post about three proven techniques for detecting targeted attacks that i would like to share. One line of defense won t protect you many will. What a senior is cyber security engineer does at fragomen.
Deep learning detection techniques. Use threat hunting techniques to scour your systems to ensure new malware has not slipped through the cracks. Malware itself or packets sent by malware in the attempt to create or leverage a security breach. Targeted cyber intrusion detection and mitigation strategies update b.
Preventative security measures such as firewalls secure web gateways and antivirus solutions can no longer defend against sophisticated cyberattacks. The uptick in new malware means prevention and detection become trickier and continuous threat hunting must become the norm. The motivations and behaviors of insider threats vary widely. Businesses faced an average of 230 000 cyberattacks according to a recent study.
Home software development software development tutorials cyber security tutorial some effective techniques of fraud detection analytics techniques to detect fraud analytics these days business data is being managed and stored by it systems in an organization. These techniques can be more challenging to implement but will provide long term value. Download the report here. And regardless of the security stack you have deployed be wary of new malware attacks.
One of the major cyber security challenges today is insider threat which results in the theft of information or the sabotaging of systems. This approach also known as knowledge based involves looking for specific signatures byte combinations that when they occur almost invariably imply bad news.