Cyber Security Metrics List

For example if users or administrators are asked if their systems comply with the orga nization s policies they are very likely to say that they do.
Cyber security metrics list. 4 cyber security metrics and measures often produce inaccurate or skewed results depending on the types of questions asked. The adage what can t be measured can t be effectively managed applies here. That said you will want to choose metrics that are clear to anyone who looks at your reporting. Choosing your cybersecurity metrics.
Security ratings can feed into your cybersecurity risk assessment process and help inform which information security metrics need attention. For the data geeks in the crowd we also really like another book entitled data driven security. There is no hard and fast list of the cybersecurity kpis and kris all businesses should be tracking. Hayden goes into significant detail on the nature of data statistics and analysis.
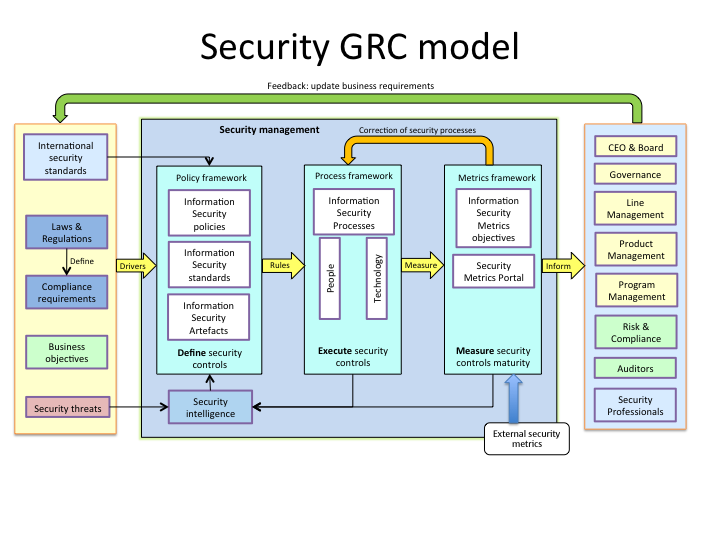
Indeed to get an accurate assessment of network security and provide sufficient cyber situational awareness csa simple but meaningful metrics the focus of the metrics of security chapter are necessary. Abstract metrics are tools to facilitate decision making and improve performance and accountability. Etc although these metrics can evaluate network security from certain aspects they cannot provide. Subject of information security metrics we really like it security metrics by lance hayden.
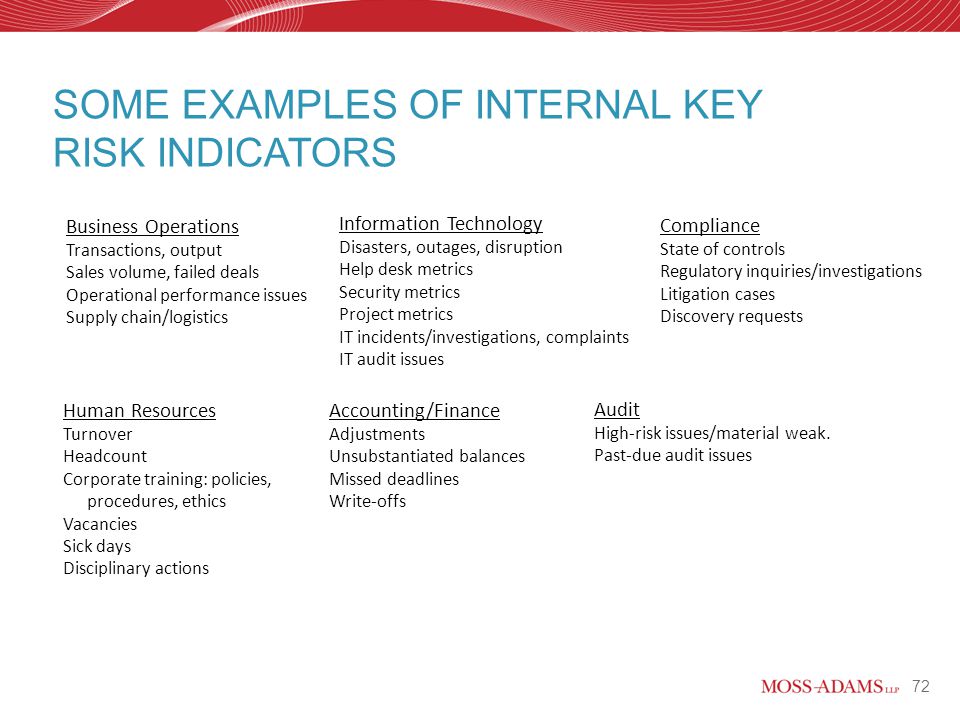
Without good metrics and the corresponding evaluation. To do that you need a list of metrics that are correlated with the effectiveness of an organization s cyber security policies. Effective management of varying performance indices in information security can mean the difference between a practical and efficient project and a complete waste of money. Measures are quantifiable observable and objective data supporting metrics.
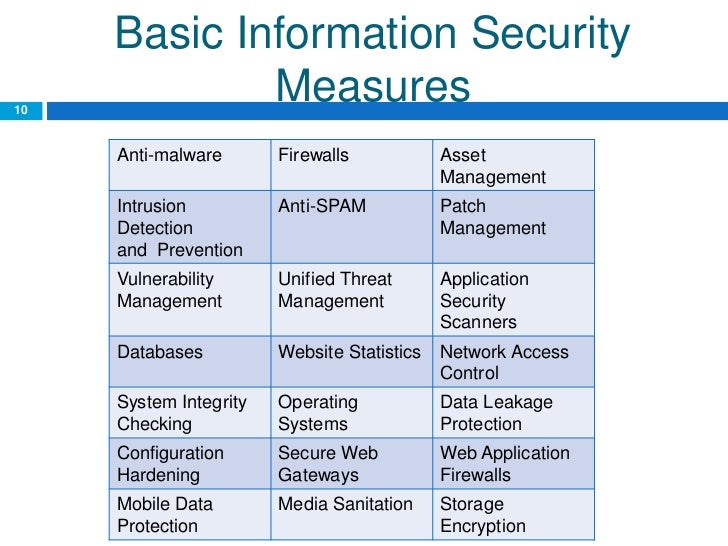
Cyber security metrics and measures. The threat landscape for your organization extends beyond your borders and your security performance metrics must do the same. Although managers have been following kpis for quite some time now in information security this is an uncommon and still developing practice to track cyber security metrics. Potential security metrics cover a.
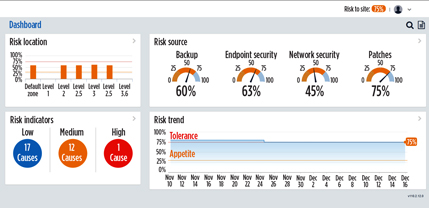
A comprehensive security audit should include relevant security metrics such as data breach response metrics time plan effectiveness number of security incidents based on specific severity levels and types of incidents such as malware infection unauthorized access destructive attacks persistent threats etc. Compliance does not necessarily equal security and you need to make sure that your customers tools and processes are actually working in order to provide the best service and close any gaps. Metrics for information and network security measurement such as the number of vulnerabilities or detected cyber incidents in a network the average response time to a security event. Analysis visualization and dashboards by jay jacobs and bob rudis.