Cyber Security Roles And Responsibilities For The Entire Workforce
Chief security officer cso head up all physical info cyber security.
Cyber security roles and responsibilities for the entire workforce. Information systems security manager. Manages the communications security comsec resources of an organization cnssi no. The role of cyber security in the organization broadly speaking cyber security is a subset of information security management that focuses on digital information and digital assets. The world of cybersecurity is ever changing and cyber attacks continue to expand in scale and scope.
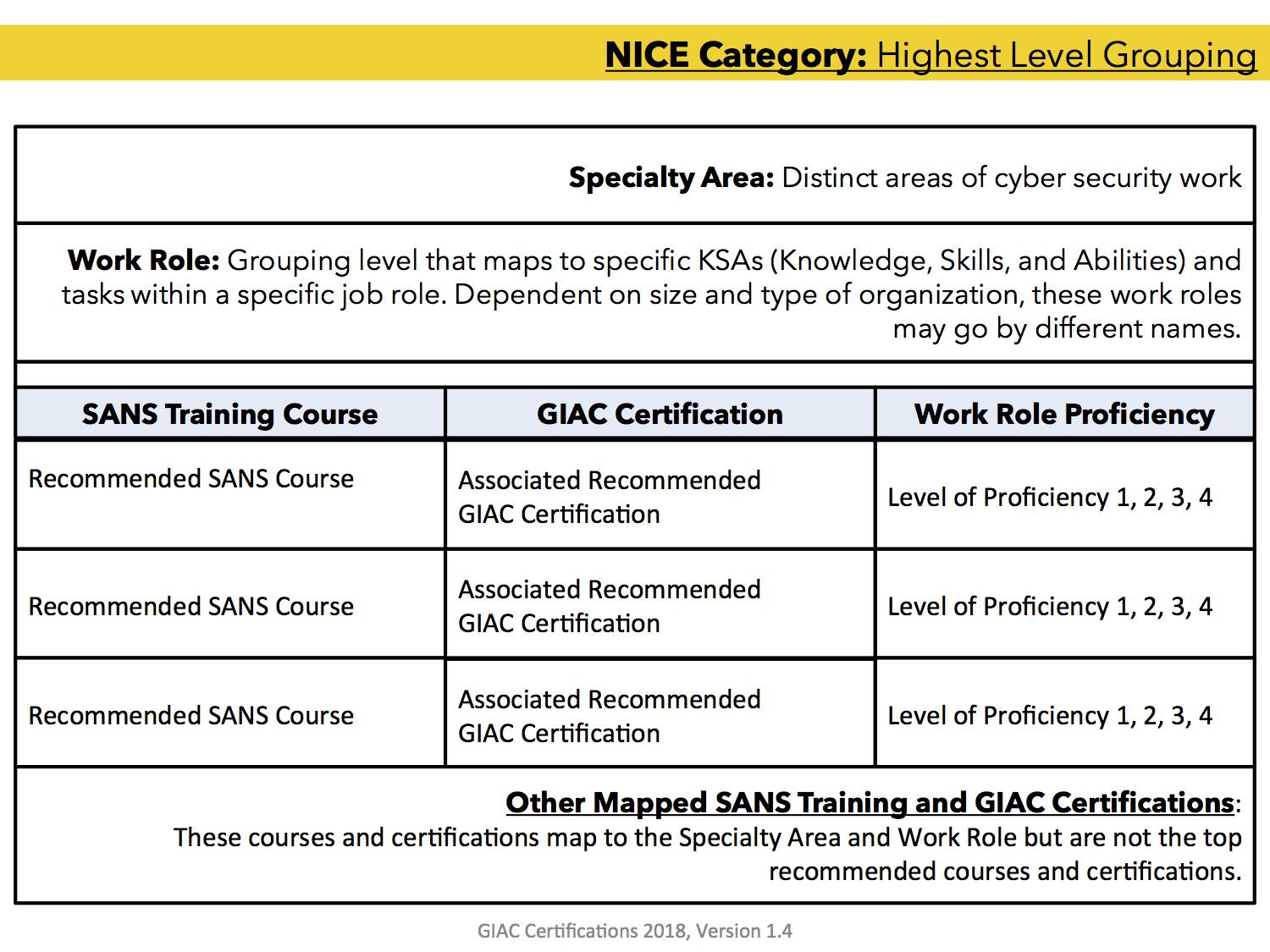
The nice framework provides a blueprint to categorize organize and describe cyber security work into specialty areas categories and new work roles. Responsibilities range in scope from the protection of one s own password to security controls administration for a large system or an entire unit. On a side note the industry still hasn t decided on a standard so this applies to cybersecurity roles cyber security roles it security roles infosec roles computer security roles or even information security team roles and responsibilities. Federal agencies will soon be using the ncwf to identify their cybersecurity workforce as called for by the federal cybersecurity workforce assessment in the cybersecurity act of 2015.
Confidentiality integrity availability. Oversees the cybersecurity program of an information system or network including managing information security implications within the organization specific program or other area of responsibility to include strategic personnel infrastructure requirements policy enforcement emergency planning security awareness and other resources. It s nearly impossible to single handedly keep up with the evolving threat environment and cybersecurity best practices especially when many information technology teams are juggling with competing priorities with limited resources. All workforce members have the responsibilities listed in section v a workforce member.
Cyber security s goal is to assure the cia of digital information within the organization. Strategic planning and policy. Cyber workforce developer and manager. Responsible for the cybersecurity of a program organization system or enclave.
Recognizing the need of a trained and certified workforce it goes further by defining critical tasks knowledge skills and abilities ksas. Cybersecurity workforce the ncwf will serve as a building block for the development of training standards as well as for individual career planning. Cybersecurity scrum master watch over and protect all data. Crafting a good cyber security job description is a big challenge because each company has different needs and has its own expectations for each role on the security team.
However you name it it falls within the same cyber security job descriptions.