Cyber Security Metrics Ppt

Due to the complexities of cyber threat mitigation ceos and boards struggle with proactively identifying the cybersecurity metrics that they need for effective governance.
Cyber security metrics ppt. R 10 unix policy checker upc yes 11. Manual dashboards created at some regular frequency. The template contains a colorful digital security powerpoint background design for the theme. R 12 application scanner appscan not used 13.
Tactical metrics focused on select security domains. R 11 hewlett packard network automation hpna yes 12. Free cybercrime prevention powerpoint template is a template for powerpoint presentations with a security symbol background. R 08 guardium metrics yes 9.
1 1 background the department of homeland security dhs federal network security fns program created. Whatever version of these slides makes sense for your enterprise will enable you to highlight metrics and how the security team is contributing to the positive outcome. Before sharing sensitive information make sure you re on a federal government site. R 13 web scanner webscan not used 14.
The gov means it s official. Effort still largely manual. Federal government websites often end in gov or mil. Nist references nist special publication 800 55 revision 1.
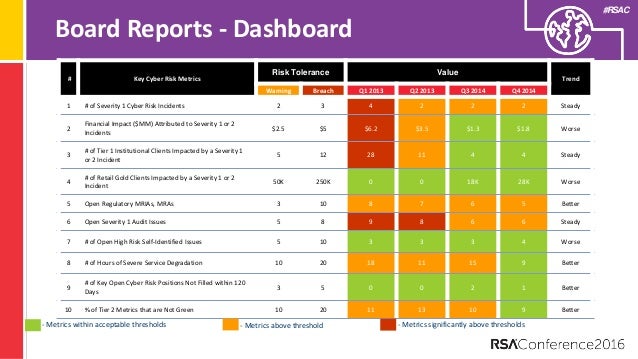
You may want to track a combination of different sorts metrics. However when presenting to the board it is key to link implicitly or explicitly security and risk to business elements that the board members value. In this report we describe threat metrics and models for characterizing threats consistently and unambiguously. Performance measurement guide for information security elizabeth chew marianne swanson kevin stine nadya bartol.
Metrics may be influenced by industry frameworks. Process security metrics measure processes and procedures imply high utility of security policies and processes relationship between metrics and level of security not clearly defined compliance governance driven generally support better security actual impact hard to define. Metrics cover most security domains. We embed these metrics within a process and suggest ways in which the metrics and process can be applied and extended.
R 09 windows policy checker wpc yes 10. R 07 tripwire metrics yes 8. It is difficult to translate all the detailed activity into summarized metrics that are meaningful for the ceo and board. Lastly and most importantly your cybersecurity benchmarking should communicate something important about your organization s security to business leaders.